>> SHELLSHOCK - WHAT IT REALLY MEANS TO IOT
Unfortunately, software bugs are inevitable and the most common source of
exploitation.

Over the past few days a lot of focus has been placed on what is known
as the Shellshock exploit that impacts all computers that use
the Bourne-Again Shell (bash). Exactly how serious is this bug and what are
the implications specifically related to the Internet of Things and why
should consumers care about this?
If you are using Mac OSX, Windows, Linux (or *NIX variant) or even a mobile
device that has bash in its core - you may be using a system that is
vulnerable to attack. It extends beyond personal computing as well;
67.4% of all web servers (source: Feb, 2014) use a
*NIX based operating system that have bash installed.
So exactly what is the Shellshock exploit?
Symantec explain it in simple terms:
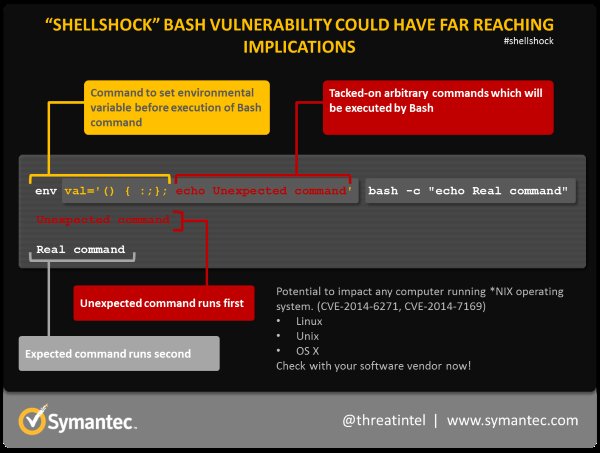
This isn't the first time we've seen panic come out of a computer bug -
just recently there was a lot of hype about the
Open SSL
bug known as
Heartbleed (original advisory). But we have also seen bugs that have existed
for 20+ years before finally get identified and fixed - such as the
BSD *dir() library (25 years),
Yacc bug (33 years) and one that even was sent to Mars with the Curiosity Rover - the
Lempel-Ziv-Oberhumer (LZO) compression (20 years).
A lot of discussion - and a very simple example has been posted on websites
such as
security.stackexchange.com and
wikipedia.org outline a series of simple examples
that could be used to obtain secret files or even remove or replace important
files. Just by setting the User-Agent: attribute while browsing a
CGI script - evil can be done; one user on
twitter posted an example that would conceptually update
(unverified) bash and reboot a server.
Running a simple test on my own Macbook Pro (in Terminal window):
The bad command is sneakily stored within the string being assigned to val -
but gets executed. The solution is to either download and compile a new
version of bash from source (too difficult for most people) or wait for
an official update from the operating system provider.
Unfortunately, as IoT devices get more processing power and memory it
is common to install a *NIX variant on them which would also make those
devices exploitable by the same attack. The
Arduino Yún,
Intel Galileo,
Raspberry Pi,
BeagleBone or any other IoT device that uses a *NIX variant as its base operating
system can be affected.
In regards to security and IoT - this is a massive vulnerability and concern.
Exploits do not always happen due to badly written software -
the majority of them, like many identified in the recent report by
Hewlett Packard stating 70% of IoT devices are insecure, are due to
flaws in the underlying operating system (openSSL, bash et al).
Even with detailed
understanding of the bug there may be even more
vulnerabilities due to the basic design of how bash was designed and the manner
in which the parser and command execution handler was implemented (being
too clever for its own good).
One of the things that I particularly like about the
Arduino
platform and by having such limited processing power is that the devices
run in what is known as "bare bones" mode - meaning that the only program
on the device is the software itself resulting in less points of attack.
As computational power increases on IoT devices, the move should be to
focus on bare bones programming - not piggy backing on *NIX based operating
systems that are more likely to be vulnerable to 0-day attacks that are
found even on desktop and server platforms that can be also applied onto
IoT based devices.
Imagine the devices already on the market with this exploit - with no
mechanism to update.