>> ARDUINO WIFISHIELD101 - AVAILABLE, BUT IS IT READY?
Security has been a hot topic for IoT - but sometimes things can be released
too early.

I reported on the
announcement of the
Arduino WiFiShield 101
a while ago but after a year of waiting; the device has been released to
the market and as such retiring the existing
WiFiShield.
Has it's introduction been a stunning hit or has it been a massive flop -
one way to find out is the review the
forums
to see the teething issues popping up and how they are being responded to.
The good news is that the
WiFi101
library is 1:1 matching the existing WiFi library so that will make
transition of existing code quite easy; just a matter of changing the
header file being included in the start of the sketch to WiFi101.h
instead of WiFi.h.
As for changes; there is now support for connecting to WPA2 Enterprise WiFi
networks and the inclusion of a new function, connectSSL that has
been provided to allow for HTTPS connections at both an IP and URL level on
a specific port. The
documentation
of the function contains something that raised my eye brows and needs clarification:
Say what - one must upload the servers SSL certificates to the shield in advance?
Tim over on the Arduino forums posted a
question
about this where he states he can connect to the arduino.cc:443 domain
as shown in the example but not his own website. After a month; the question
doesn't seem to be answered so it does raise some concerns - also, the procedure
to upload a new SSL certificate isn't available yet; so how useful is the
shield right now?
Another community member raises the
concern
about the amount of space the WiFi101 library uses - just a very basic
setup where the scan for network stage is met and it uses 59% of the
available flash on the Arduino UNO, not leaving much for doing anything else.
It would be interesting to know exactly what level of transport layer security
is actually supported - given the limited memory of the devices processing
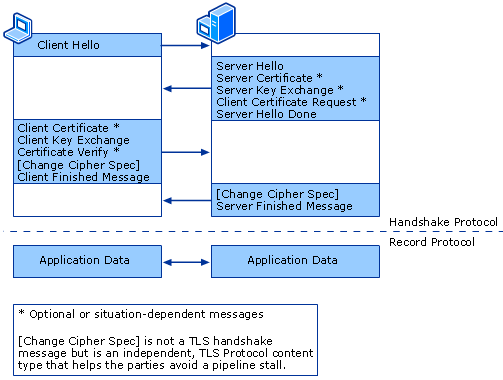
a X.509 certificate is quite difficult on the low powered devices. One user
has outlined the various
methods
(basics shown below) behind SSL/TLS - it looks like the library may only
support RSA key exchange where the client encrypts 48 bytes (46 random)
with the servers public key and there is no ServerKeyExchange.
I will keep an eye on the discussion and watch how the documentation
gets updated - but I think there needs to be a little clarification on
how the shield actually works and what level of TLS is supported before
one dives in and purchases these for production. It looks like it needs a
little move love to mature before being ready for the market.